Opening a job email titled “Bewerbung via Arbeitsagentur – Eva Richter” (Application via Employment Agency – Eva Ritcher) could prove disastrous to you, according to a new report.
Bleeping Computer, a website dedicated to reporting on Cybersecurity, confirmed the existence of an “Eva Ritcher” fake resume scam. The scam targets people in Germany by attaching a malicious “.exe” file, in the email, possing as a PDF resume application.
This new scam works similar to a Ransomware in its function. It first encrypts files on the computer then asks for extortion money, in the form of Bitcoins, to decrypt the files.
“Eva Ritcher” Fake Resume: How Does It Work?
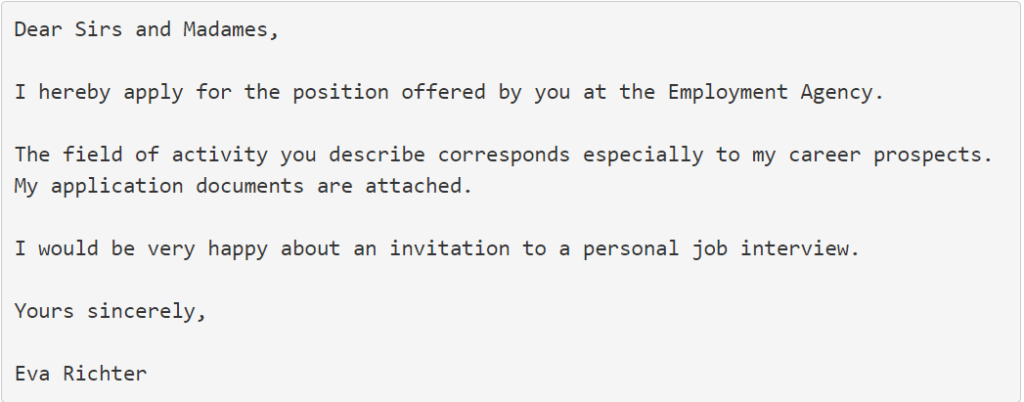
“Eva Ritcher” fake resume scam poses as a job application e-mail claiming to be from an employment agency. The text of the e-mail reads:
This e-mail also contains a file named “Eva Richter Bewerbung und Lebenslauf.zip” (Eva Ritcher Application and CV.zip).
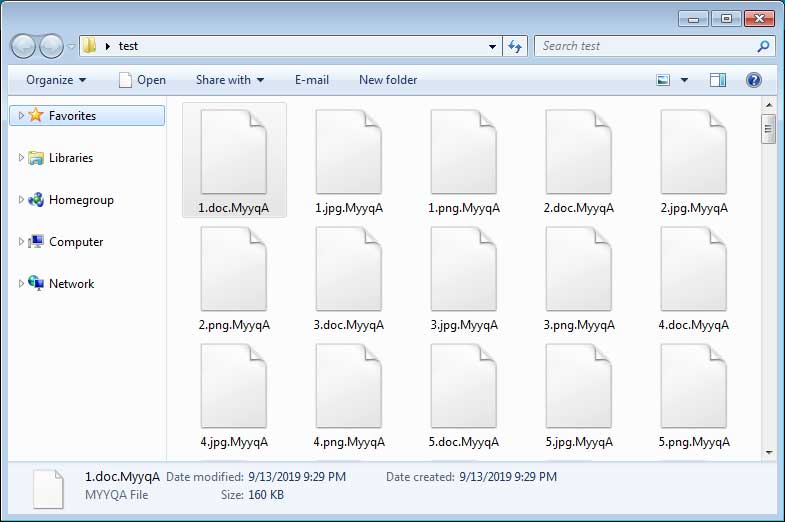
Inside the zip file is a resume and stock photo, both of which claim to belong to Eva Ritcher. The scammers use a “custom-icon” and “double extension” technique to trick users into opening malicious files.
The resume has a PDF icon but while checking its extension you can see that it’s a “.exe” file instead.
Specifically, it is an Ordinypt installer. According to the Bleeping computer, it flashes the screen a few times. After that, the malware begins to encrypt files on the computer.
Philipp Mackensen, a reverse engineer, described the Ordinypt as a wiper disguised as ransomware. He explained that Ordinypt exchanged the data of the files with random lowercase, uppercase letters, and symbols while destroying the original ones.
The Ordinypt in this instance works like ransomware as well as a wiper: a malicious program that destroys files while encrypting them.
Here, the installer encrypts the files, disables the Windows 10 recovery environment and ends all processes while deleting shadow volume copies. Moreover, the encryption it performs involves filling the files with a bunch of random data, making them incomprehensible to read.
Ordinypt creates pseudo-files of the original documents meaning it destroys one-half of the file data while encrypting the other half. It also adds a custom extension to all encrypted files for identification.
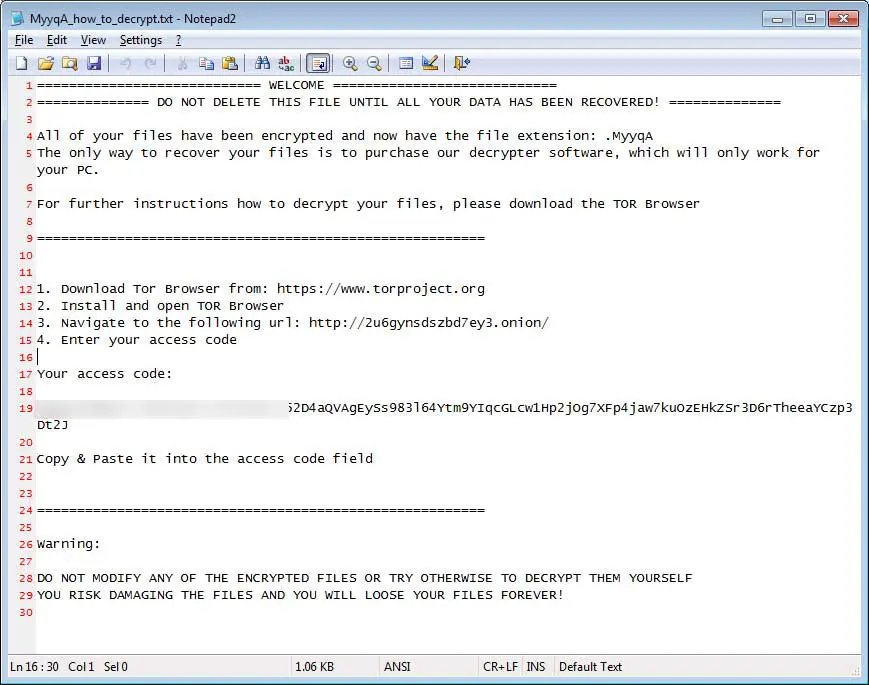
After completing the encryption/destruction of data, the Ordinypt leaves a ransom note [extension]_how_to_decrypt.txt. It directs the user to a Tor site to make a payment of around 0.1473766 BTC which amounts to $1,518.97.
The report on the Ordinypt advises to not make payment to these scammers. This is because Ordinypt destroys the user’s files when it encrypts them.
According to the report, in several cases, Shadow Volume Copies managed to survive the Ordinypt. In this case, you can recover your files.
For the uninitiated, the Shadow Volume Copies is a tech introduced by Microsoft in 2001 with Microsoft Windows XP Service Pack 2. It creates an automatic backup of your files on any one section of your hard drive.
Early Encounter With Ordinypt
This isn’t the first time the Ordinypt is posing as a fake resume to wreak havoc on users. It was initially discovered by Michael Gillespie.
In 2017, the Ordinypt was being distributed in a similar way, via a fake resume email. The only difference is that the name of the fake applicant was “Viktoria Henschel” instead of “Eva Ritcher.”
The method of attaching a malicious file via resume application was previously used by Petya Ransomware, which encrypted not files but entire sections of the hard drive, only to unlock it in exchange for a hefty payment.
In order to stay safe from these kinds of online attacks always follow the following rules:
- Update your virus definition regularly.
- Keep an offline backup of your data in a separate hard drive.
- Keep your firewall ON and always check the nature, extension, and type of the file before you open it.
Also Read: Thousands Of Linux Servers Infected By Lilu (Lilocked) Ransomware