Not to be morbid, but the COVID-19 pandemic has come at a perilous time for the enterprise firewall vendors that rely heavily on selling big iron (and that’s most of them). During the stay-at-home quarantine, nearly every user who was previously “inside” a next-generation firewall (NGFW) perimeter is now exiled outside, and many may never return. The user exodus, coupled with the fact that most enterprise applications graduated to the cloud years ago, has diminished the value proposition of an expensive, north-south, inspection zone appliance.
But this stay-at-home springtime might be an opportunity for a new generation of firewall technology. Before we get into exactly what that new generation is, let’s review the evolutionary path that got us here.
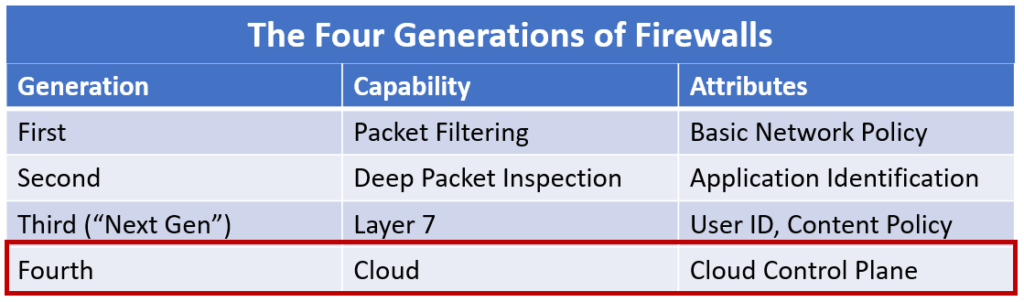
The first generation of firewalls included proxies and packet filters, providing perimeter security with policy based on networks and ports (ISO layers 3 and 4). These early firewalls proved quite porous, and wave after wave of threats swarmed through them. Attackers and malicious insiders bypassed them by merely changing the ports of their traffic, creating tunnels through ports 80 and 53 (DNS).
The second generation of firewalls featured deep packet inspection (DPI) to combat the tunneling problem. These newer firewalls identified the real protocol of a connection, regardless of the ports that were selected. However, they did little to mitigate a new main threat: users inside a perimeter blithely clicking away on malicious links and bringing malware home to the enterprise.
The third generation (or “next generation”) of firewalls (NGFW) debuted in 2007. In 2008–2009, as the world grappled with a “once-in-a-lifetime” financial crisis (ha!), the NGFW grabbed network security mindshare as it solved the malware problem by incorporating IDS/IPS and automated malware analysis (AMA) into its policies. By necessity, the NGFW had to parse layer 7 traffic, and eventually decrypt outbound internet traffic, to finally give the firewall operator visibility into user browsing activity. It’s been 13 years (!) since the introduction of the next-generation firewall, and the name seems not so new, right?
That brings us back to the present. Forrester just published our new research on the enterprise firewall market in the report “Now Tech: Enterprise Firewalls, Q1 2020.” In it, we present our findings on the market’s vendors and major functionality groups.
We’ve found that enterprise firewalls are extending policy control around native public cloud objects. Multiple enterprise firewall vendors have solutions where the firewall software itself isn’t in the data plane but instead its console manages the security policy of the public cloud objects.
A single management plane for network security that covers on-premises and public clouds is significant enough that it should rightly be crowned as the fourth generation of firewalls (FW4, for short). The familiar consoles and policy engines can abstract away the differences in multiple public cloud security approaches, each with their own APIs and oddities.
Executing properly on the FW4 approach will make the enterprise firewall “sticky” to the security team as they inherit responsibility for the organization’s cloud objects, even as the users follow the applications out to the cloud.
This summer, Forrester will be refining its definition of FW4 in forthcoming network security and infrastructure research. Until then, read our Forrester report, “Now Tech: Enterprise Firewalls, Q1 2020,” to see the lineup of 18 players in large, medium, and small firewall markets.