Twitter lost control of its internal systems to attackers who hijacked almost a dozen high-profile accounts, in a breach that raises serious concerns about the security of a platform that’s growing increasingly influential.
The first signs of compromise occurred around 1pm California time when hijacked accounts—belonging to former Vice President Joe Biden, Elon Musk, Bill Gates, and other people with millions or tens of millions of followers—started pumping out messages that tried to scam people into transferring cryptocurrency to attacker-controlled wallets.
In a tweet issued about seven hours after the mass takeover spree began, Twitter officials said the attackers appeared to take control by tricking or otherwise convincing employees to hand over credentials.
“We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools,” the tweet said. “We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.”
We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.
— Twitter Support (@TwitterSupport) July 16, 2020
Once Twitter learned of the takeovers, company personnel locked down the accounts and removed the tweets. Twitter’s tweet thread didn’t explain why Musk’s account posted fraudulent tweets after previous ones had been deleted.
Bad for national security, too
The compromise raises serious national security concerns because of the potential it had to sow panic and chaos. With control of virtually every Twitter account, the attackers could have hijacked those belonging to President Trump or government agencies and done much worse than replay a cryptocurrency scam that has been going on for years. Twitter eventually contained the mass compromise but only after a flood of scam messages steadily flowed out of the social media site over several hours.
It’s not the first time Twitter has suffered a serious breach of this sort. In 2010, the company settled Federal Trade Commission charges for lapses that allowed hackers to obtain unauthorized administrative control of internal systems. The breach, the FTC said, gave the attackers access to user data and private tweets and the ability to make phony tweets from any account including those belonging to then-President-elect Barack Obama and Fox News.
Just hours after Wednesday’s breach came to light, US Senator Josh Hawley sent a letter to Twitter CEO Jack Dorsey asking that he contact the FBI to make sure the site is secure.
“I am concerned that this event may represent not merely a coordinated set of separate hacking incidents but rather a successful attack on the security of Twitter itself,” Hawley wrote. “As you know, millions of your users rely on your service not just to tweet publicly but also to communicate privately through your direct message service. A successful attack on your system’s servers represents a threat to all of your users’ privacy and data security.”
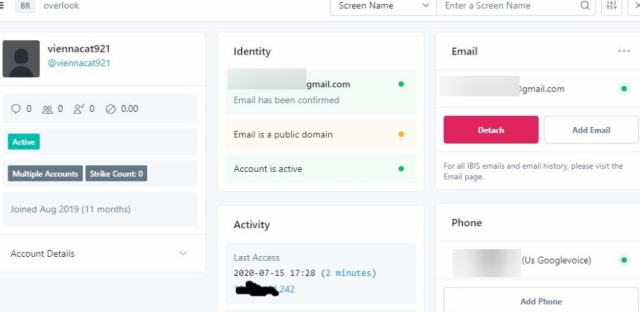
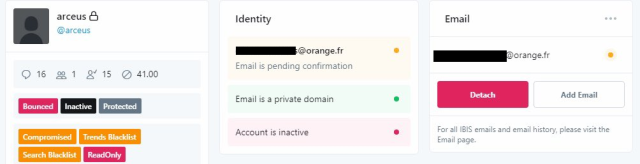
An article posted by Motherboard, citing unnamed hackers and corroborating screenshots, said the attackers gained access by paying a Twitter insider. The post went on to show a panel controlling the account of Binance, a cryptocurrency exchange whose Twitter personna was hijacked.
Other screenshots that circulated widely showed what purportedly were screenshots of Twitter administrative tools. While the screenshots haven’t been confirmed, Twitter repeatedly took two of them down and terminated the account of a person who initially posted them. Hackers and security people said they considered them plausible. The two initial screenshots appear below:
Adrian Lamo’s coveted Twitter handle targeted, too
Besides those of celebrities, business leaders, and politicians, the Twitter account of Adrian Lamo—a hacker known for high-profile exploits and for turning in Chelsea Manning and who died in 2018—was also compromised on Wednesday under similar circumstances.
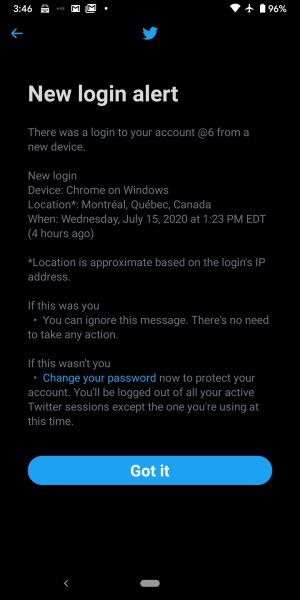
Fellow hacker and friend Lucky225, who has had control of the account since Lamo’s death (with the blessing of his father), said Twitter sent him a password reset confirmation code for the account at 10:23am California time, about 90 minutes before the first public signs of a breach. Despite not entering the code, Lucky225 (his legal name, he says) then received an app notification warning him a new device had logged in to the Lamo account for the first time.
Lucky225
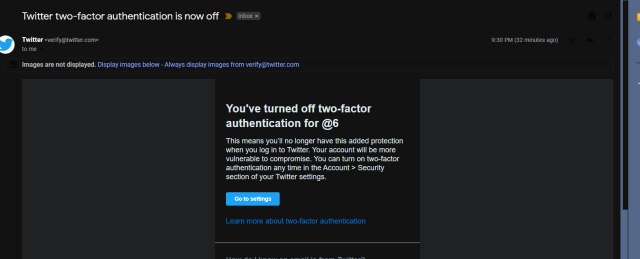
In a stroke of luck, Lucky225 said he was able to regain control of the account because, while the hackers had changed the email address associated with the account, they had failed to change the phone number. Lucky225 said he used the phone number to regain control. Then, in a strange and currently unexplained twist, Lamo’s friend said that at 8:30pm he discovered the account had again been hijacked—or at least partially so—when Twitter emailed him again to say two-factor authentication had just been turned off.
Lucky225
“What’s weird.. the password (which was just randomly generated in PW manager today when I recovered the account earlier) still works,” Lucky225 told me in a text message that dropped and abbreviated some words. “But when I use it to login it says account’s locked. And then wants me to change my pw to continue but won’t actually let me do that since email was apparently changed.”
He said it’s possible that Twitter is behind the second takeover because company employees mistakenly believed the account was still compromised. Another possibility is that hackers somehow managed to force their way back in by exploiting a vulnerability in several third-party apps that, through the OAuth protocol, had permission to access the Lamo account.
Lucky225 said he suspects attackers targeted Lamo’s account for its handle—@6—which at a single character, is highly coveted by many hackers. He’s not sure if the same hackers were responsible for the hijackings of both the Lamo and celebrity accounts, but he said the ability to twice bypass 2FA and password controls suggests whoever is behind the Lamo account takeover had control of internal Twitter systems.
A Twitter spokeswoman said the company had nothing to add beyond the information in the tweet thread.
Twitter account holders should follow the usual security guidance to lock down accounts. The advice includes using a strong password (unique to the account, randomly generated using either dice words or letters, numbers, and special characters), 2FA, and to turn on Twitter’s password reset protection, which requires users to provide additional information before a passphrase can be changed. Given that those measures were bypassed on Wednesday, they may not be enough.
