Researchers have uncovered the first instance case of a cryptojacking worm that propagates via malicious Docker images, according to Palo Alto Networks’ threat intelligence team Unit 42.
Dubbed “Graboid,” the worm infects compromised hosts with malware that covertly abuses the systems to mine privacy-focused cryptocurrency Monero before randomly spreading to the next target.
Docker is a popular platform-as-a-service (PaaS) solution for Linux and Windows that allows developers to deploy, test, and package their applications in a contained virtual environment (called “containers”) — in a way that isolates the service from the host system they run on.
It’s also similar to a virtual machine, but unlike the latter, containers don’t require a whole virtual operating system. Instead, it enables apps to share the same system resources and are shipped only with those components they need in order to operate, thereby reducing their overall size.
Upon alerted by Unit 42, Docker removed the malicious images — a shareable “digital snapshot” of a pre-configured application running on top of an operating system — from Docker Hub, a code repository from where they had been downloaded more than a collective 16,000 times.
As businesses increasingly migrate to the cloud, the research underscores the need to beef up security conrols or else risk getting exposed to targeted reconnaissance, the cybersecurity firm said.
“We’re continuing to see instances where the failure to properly configure containers can lead to the loss of sensitive information and as a result, default configurations can be significant security risks for organizations,” Unit 42’s Senior Cloud Vulnerability and Exploit Researcher Jay Chen told TNW.
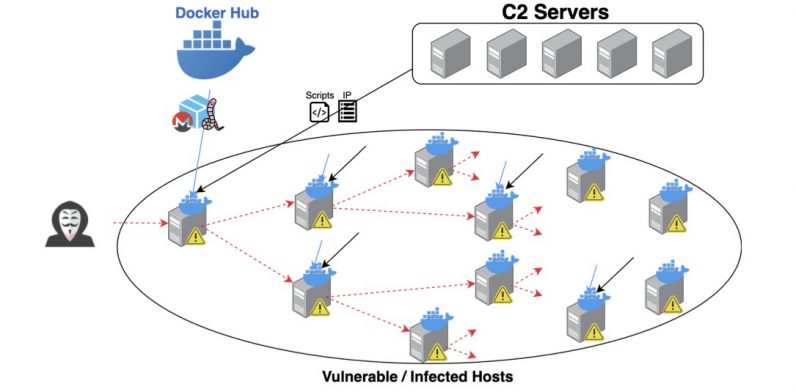
The worm propagation
Unit 42 said it discovered the worm late last month after the same malicious image in question appeared across several unsecured Docker hosts discovered via Shodan, a search engine used to identify systems that are connected to the internet.
Once remotedly deployed and installed, the contaminated container image — which also comprises of a program to contact other hosts — connects to a remote command-and-control server to periodically query for vulnerable hosts and select a target at random to spread the worm.
“We have a growing concern attackers will continue to exploit these issues in unpatched instances to spread their footprint by escaping containers and gaining persistence on the container hosts and more can definitely be done to secure them,” Chen told TNW. “Many of these malicious images are disguised as other popular container images while containing a backdoor, sometimes retaining the original image’s functionality to avoid getting detected.”
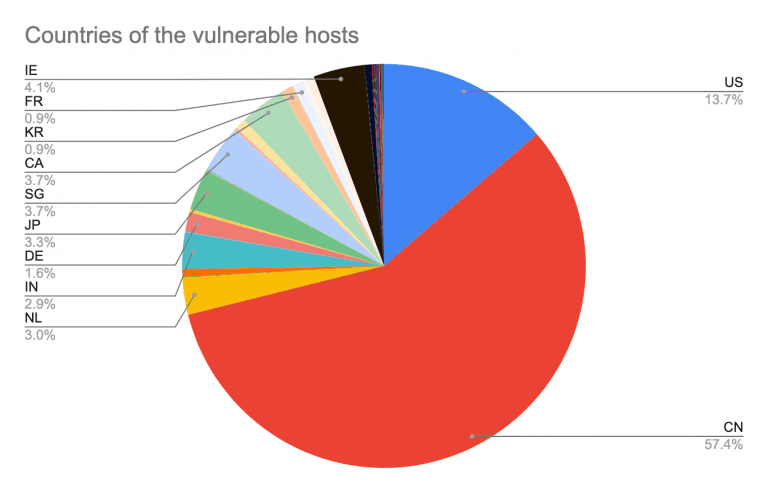
The threat actor leveraged over 2,034 vulnerable hosts this way, Unit 42 said, stating that 57.4 percent of the IP addresses originated from China, followed by 13 percent from the US, and that there are, on average, 900 active miners at any given point of time.
The takeaway
This is far from the first time the container architecture has been exploited to install cryptocurrency-mining malware.
Previous disclosures from Trend Micro and Imperva have found exposed Docker hosts to be an actively abused attack surface in cryptojacking operations that make use of Shodan to discover and infect more victims.
It’s not just Docker. Similar instances of exposed hosts have been uncovered on Kubernetes — an open-source PaaS system originally designed by Google — as well.
“We haven’t observed this specific worm in Kubernetes, but earlier this year, our research found that some 20,353 Kubernetes [containers] around the world operate under default configurations,” Chen told TNW. “This doesn’t necessarily mean that these platforms are vulnerable to exploits, but it demonstrates that seemingly basic misconfiguration practices exist in large quantities and as attacks continue to evolve, it will make organizations targets for further compromising events.”
Although Graboid’s tactics and techniques aren’t sophisticated, it’s crucial that organizations secure their Docker hosts, monitor their network traffic, and most importantly refrain from downloading Docker images from unknown sources.
“As your organization’s cloud footprint grows, being able to automatically model and whitelist application behavior becomes a powerful tool for securing cloud workloads against attacks and compromises,” Chen said.
Read next:
The rate of the universe’s expansion is in dispute – but a new kind of measurement offers hope